As major technological advancements – ones that are both rapid and ongoing, in this day and age – spread across branches of society, threats to security have also evolved. We talk a lot about cybersecurity in relation to the Internet of Things, but such threats also hit physical infrastructures, as well; this jeopardizes safety, economics, and system reliability as a whole. As the scope of threats expands, the challenges in strengthening protection measures grow. Unifying physical and technological security mechanisms for organizations is vital. The Cybersecurity & Infrastructure Security Agency (CISA) has backed this; the sobering reality is that roughly 47% of American adults have had their information (both personal and professional) exposed by criminals (cyber or otherwise), and 83% of millennials currently agree that awareness programs in school and at work are more important now than they’ve ever been.
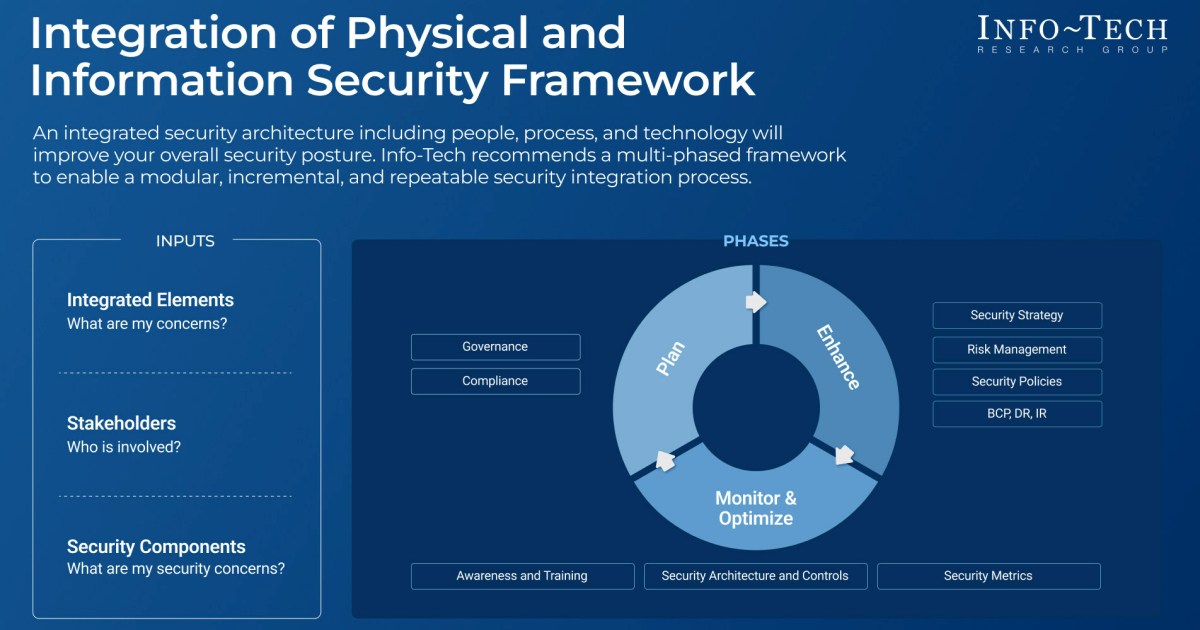
So, to help individuals and organizations address the pressing needs for unifying both physical and information security mechanisms, global research and advisory firm Info-Tech Research Group has published its latest blueprint for success via findings from its “Integrate Physical Security and Information Security” plan. Info-Tech’s latest resource highlights recommended approaches to the “modular, incremental, and repeatable processes necessary to integrate physical and information security.”
The steps, as prescribed by Info-Tech:
- Plan and engage. Assemble the right team to ensure the implementation of the appropriate integrated security system(s). Per Info-Tech, it’s “absolutely essential to decide on the governance model and clearly define roles and responsibilities.”
- Enhance strategies and risk management protocols. What this boils down to is the development of a physical security system that is easily interoperable with most modernized technologies. The design should “be flexible, require minimal customization, and remain intuitively functional and integrated,” even when the challenges include “proprietary configurations and siloed operations statuses.”
- Deploy, monitor, and optimize. Once the best strategic, realistic, and risk-based architectural design has been identified, perform an evaluation of the applicable security systems and “program by understanding what, where, when and how to measure and report the relevant metrics for future analyzation and enrichment.”
Info-Tech stresses this point about physical security in tandem with key cybersecurity roadmaps because “everything must be considered for facilities management.” There are new interdependencies with both internal departments and external parties and how they function in today’s world. As Info-Tech has written, “Physical security systems integration can be complex due to a blend of proprietary devices, protocols, and the coexistence of analog and digital technologies.”
According to Carlos Rivera, Principal Advisory Director at Info-Tech:
“The convergence of operational technologies (OT) and the Industrial Internet of Things (IIoT) is transforming widespread security landscapes. This convergence is being driven by the adoption of sophisticated access control systems, including electronic locks and biometrics, as well as the digital evolution of security through cloud technologies. So, as organizations face increasing risks, the long-term benefits of a consolidated strategy to address the many faces of modern security is a must.”
In its published plan, Info-Tech also covers security visibility needs, staffing and training programs for awareness, emergency mitigation plans, and more. That, again, is found here.
Edited by
Greg Tavarez





